Biometrics is the science of using digital technology to identify individuals based on the individual's unique physical and biological qualities. Simply, biometrics is the technique of verifying a person's identity from a physical characteristic (i.e., fingerprint, hand print, face, scent, thermal image, or iris pattern), or personal trait (voice pattern, handwriting, or acoustic signature).
The modern biometric device was introduced commercially over 20 years ago when a machine that measured finger length was installed for a time-keeping application at Shearson Hamil on Wall Street. There are now over 10,000 computer rooms, vaults, research labs, day care centers, blood banks, ATMs, and military establishments to which access is controlled using devices that scan an individual's unique characteristics. .
contents
1)classification
2)Enhancing privacy & secutrity
3)Biometric Technologies
4)Feature Developments
5)Applications 6)Terminology
7)Conclusion
Classifications of biometrics:
There are two types of classification.
They are 1)physiological characteristics.
2)Behaviral Ones
1)physical characteristics: It identifes include finger prints,hand geomentry,eye patterns and facial features.
2)Typical behavioral idetifers voice and signature.voice print and signature analyzers are generally considered less conclusive because they are subject to limitations such as illness and imitations.
Biometrics are automated methods of recoh as illness and imitations.
Enhancing security and privacy in biometrics-based authentication systems
Biometrics-based authentication offers several advantages over other authentication methods, there has been a significant surge in the use of biometrics for user authentication in recent years. It is important that such biometrics-based authentication systems be designed to withstand attacks when employed in security-critical applications, especially in unattended remote applications such as
e-commerce .
The prevailing techniques of user authentication, which involve the use of either passwords and user IDs (identifiers), or identification cards and PINs (personal identification numbers), suffer from several limitations. Passwords and PINs can be illicitly acquired by direct covert observation. Once an intruder acquires the user ID and the password, the intruder has total access to the user's resources.
For example, when a user ID and password is shared with a colleague there is no way for the system to know who the actual user is. A similar situation arises when a transaction involving a credit card number is conducted on the Web. Even though
the data are sent over the Web using secure encryption methods, current systems
are not capable of assuring that the transaction was initiated by the rightful owner
of the credit card. In the modern distributed systems environment, the traditional
authentication policy based on a simple combination of user ID and password has become inadequate. Password systems are prone to brute force dictionary attacks.
Biometric systems, on the other hand, require substantially more effort for mounting such an attack.
----------------------------------------------------------------------------------------------------------
Method Examples Properties
----------------------------------------------------------------------------------------------------------
What you know User ID Shared
Password Many passwords easy to guess
PIN Forgotten
What you have Cards Shared
Badges Can be duplicated
Keys Lost or stolen
What you know ATM card + PIN Shared
and What you
have PIN a weak link
(Writing the PIN on the card)
----------------------------------------------------------------------------------------------------------
Human Recognition Systems works with 4 key biometric technologies
01. Fingerprint Recognition
02. Iris Recognition
03. Hand Recognition
04. Facial Recognition
01. Fingerprint Recognition
Fingerprints are perhaps the first biometric that comes to mind when first considering this technology as a means of enhancing your security. This is partly because in many minds biometrics are synonymous with security and identification and fingerprints are of course the primary means of positive identification among law enforcement agencies the world over.
In essence, fingerprint verification looks at the patterns found in the fingertip. There are a variety of technical approaches in this area, ranging from emulating the traditional police method of matching minutiae (the unique patterns on the surface of the fingertip) to standard pattern comparison. At the point of identification, the fingerprint is processed and a mathematical representation produced; this is then compared to an electronically-held template or set of templates, previously captured, for verification.

Fingerprints are a distinctive feature and remain invariant over the lifetime of a subject, except for cuts and bruises. As the first step in the authentication process, a fingerprint impression is acquired, typically using an inkless scanner. Several such scanning technologies “Typical scanner” digitizes the fingerprint impression at 500 dots per inch (dpi) with 256 gray levels per pixel. The digital image of the fingerprint includes several unique features in terms of ridge bifurcations and ridge endings, collectively referred to as “minutiae.”
02. Iris Recognition
Eye Recognition:
Two distinct parts of the human eye can be used to positively identify the identity of an individual: the iris or the retina. The technology has similarly taken 2 paths
when it comes to authentication and identification using the eye.

Iris Recognition:
The iris is the outer visible part of the eyeball responsible for protecting and directing light to the retina, crudely speaking. But the iris is in fact a complex structure which may be used to uniquely identify an individual and which also does not alter dramatically with age. The technology employs image capture techniques to create an image of the iris. This is processed by a proprietary algorithm to create
a representative template which in turn is compared to previously captured templates in order to identify or authenticate the identity of the individual.
Retina Scanning:
The alternative method of authenticating the identity of an individual using the eye is via retina scanning. This technology employs a more intrusive technique by way of requiring the individual to place their eye close up to a binocular or monocular type device. However, retina scanning is highly accurate and has been in use for military applications since the early seventies. The principle behind retinal scanning is that blood vessels at the retina provide a unique pattern which may be used as a tamper-proof personal identifier. To read this characteristic, a small beam of coherent light is beamed through the cornea to illuminate the blood vessels which are then photographed and analysed.

03. Hand Geometry Recognition

Hand geometry was one of the first biometrics to prove practical in use across a
variety of real-world applications. Hand geometry systems work by taking a 3-dimensional view of the hand in order to determine the geometry and metrics around the finger length, height and other details. Leading hand geometry biometrics systems measure up to 90 parameters. This information is processed via proprietary algoritham and a representative template is created accordingly for the individual concerned. An important consideration with hand geometry is that an individual's hand does not significantly change after a certain age. Once the representative template has been created, it is compared to a single or set of pre-recorded templates for authentication or identification.
04. Facial Recognition
The facial recognition method analyses the patterns in individual faces. Similar to the ay in which we recognize friends and family amongst a group of people by focusing on their faces, a facial recognition biometric system takes images from standard capture techniques such as digital pictures and generates a mathematical representation of the human face. This is compared to a template or set of templates, held electronically on a central system, to authenticate or identify an individual.

What factors contribute to a biometric feature's development?
Biometric traits develop:
through genetics: genotypic
through random variations in the early phases of an embryo's development: randotypic (often called phenotypic)
or through training: behavioral
As a rule, all three factors contribute to a biometric trait's development, although to varying degrees. The following table rates the relative importance of each factor (o is small, ooo is large):
------------------------------------------------------------------------------------------------------------
Biometric Trait genotypic * randotypic * behavioral **
------------------------------------------------------------------------------------------------------------
Fingerprint (only minutia) o ooo o
Signature (dynamic) oo o ooo
Facial geometry ooo o o
Iris pattern o ooo o
Retina (Vein structure) o ooo o
Hand geometry ooo o o
Finger geometry ooo o o
Vein structure of the back of hand o ooo o
Ear form ooo o o
Voice (Tone) ooo o oo
DNA ooo o o
Odor ooo o o
Keyboard Strokes o o ooo
Applications for Biometrics
There are an endless number of applications to which biometric technology can be applied. Wherever the authentication of an individual's identity is important to the security process there is an opportunity to deploy biometric technologies. At Human Recognition Systems, we offer a variety of "out of the box" and in-house developed solutions to address your needs. To give you some idea of ways in which biometric technology can enhance your security whilst reducing costs, here are a few examples of biometric applications:
->Airports Corporate Education Government
->Time & attendance
->Worker access
->Passenger fast track Network security
->Application security
->Laptop security
->Intranet security
->Class registration
->Examination identity authentication
->Cashless catering systems
->Employee record check
->Network security
->Document security
->Voter authentication
->PC security
->Store Network Security
->POS transaction security
->Stock room security
->RF Device control
->QA Sign-off
Biometric Terminology
Before considering all the various biometric technologies, it is important to understand some of the common terminology often associated with biometric systems:
Biometric Template:
Common to all biometric technologies is the requirement to create a biometric template. This is a digital representation of the biological phenomena, be it a fingerprint, iris scan or voice pattern. The template is generated from the captured biometric image via a proprietary algorithm. In essence a unique digital "key" is created to identify the individual. It is important to note that the biometric image cannot be recreated from the biometric template. This has been a conscious decision by all vendors to offset any "Big Brother" type concerns.
Enrolment:
In order to capture the initial or Master Biometric Template, it is necessary to enrol each and every user who will identified or verified by the biometric system. For example, when a user joins a company, as part of the standard enrolment process, you would capture their biometric template in order to give them the necessary security access.
Verification Vs Identification:
Verification refers to the verification or authentication of a claimed identity. In other words, the user wishes to log on to a network or service, or undertake an on-line transaction and claims to be a certain person. The verification process seeks to authenticate this claim via the provision of a biological characteristic or multiple characteristics known to be associated with the claimed identity. There is therefore a one-to-one matching process involved. Identification seeks to identify a user from
within a population of possible users, according to a characteristic, or multiple characteristics which can be reliably associated with a particular individual, without an identity being explicitly claimed by the user. The key difference here being a one-to-many matching process.
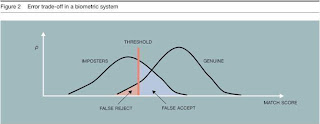
False Acceptance Rate
Also known as FAR. Measures how frequently unauthorized persons are accepted by the system due to erroneous matching. Potentially serious.
False Rejection Rate
Also known as FRR. Measures how frequently registered users are rejected by the system. This usually amounts to nothing more than inconvenience, since it requires users to try again.
In biometrics FAR/FRR are not theoretically ascertainable, instead they must be determined statistically in costly tests. Determining statistical significance is equally difficult. There were no standardized techniques, therefore results could vary due to differences in test conditions and sample size. Clarity was only provided by disclosure of the test conditions.
How is the Failure-to-Enroll Rate (FER/FTE) defined in detail?
Due to the statistical nature of the failure-to-enroll rate, a large number of enrollment attempts have to be undertaken to get statistical reliable results. The enrollment can be successful or unsuccessful. The probability for lack of success (FER(n)) for a certain person is measured:
FER(n) = Number of unsuccessful enrollment attempts for a person (or feature) n
--------------------------------------------------------------------------------
Number of all enrollment attempts for a person (or feature) n
These values are better with more independent attempts per person/feature. The overall FER for N participants is defined as the average of FER(n):
Conclusion
Biometrics offers many advantages to the law enforcement community. These advantages fall into two distinct areas, but are not mutually exclusive. Firstly, the business, process, cost and security advantages that biometrics bring to any organisation can be applied throughout the CJS, which is a collection of agencies, all of which have premises and data to protect. Secondly, there are the direct advantages to law enforcement itself as applied to the two major objectives of the prevention and detection of crime.
Identification always plays a part in crime investigation and conviction in a fair and just system. Clearly, there is a wealth of experience and expertise already applied in these fields and technology is enhancing them at a rapid pace. However, biometrics opens up new possibilities and challenges, which may increase dramatically the effectiveness of the law enforcement community.

No comments:
Post a Comment